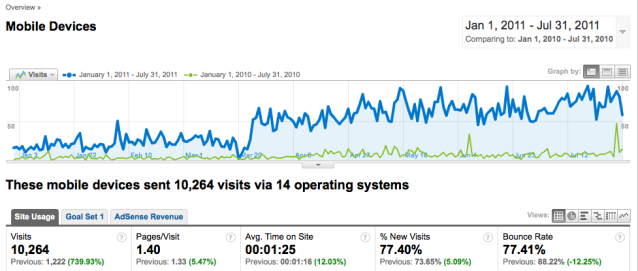
Check this out. Silent Circle is a subscription service that promises to deliver a secure and encrypted communications platform. Phil Zimmermann put this concept together and he is marketing this thing for security professionals with the help of some former Navy SEALs.
What I like about this service is that companies could actually set up accounts with contractors/employees using Silent Circle, and know that the communications between all parties will be secure. From the phone calls to text messages to emails–the entire communications system will be secure and extremely difficult to hack.
Families can also be a part of a separate Silent Circle account between the contractor and their loved ones/friends. This is great because today’s enemy’s and hostile governments all have a desire to hack into the accounts of folks involved with security operations throughout the world. They monitor everything from Facebook and Twitter accounts, to emails/phone calls etc. You have to assume all of that is happening, and to have any tools to help in the battle to secure your communications is a good thing. –Matt
Silent Circle
When a Silent Circle subscriber makes a phone call, sends a text or video chats with another Silent Circle member, that transmission is secured and encrypted end-to-end from the iPhone, Android, iPad or computer on our crystal-clear secure network. Silent Mail is an elegant and encrypted email solution, however, it utilizes server side key encryption not peer-to-peer. Our Silent Phone, Silent Mail and Silent Text products also allow you to call or send/receive emails to anyone in the world – any phone number – any email address, even to those not in our secure Circle (subscribers). Our products download from the Apple App Store, Android Play Store and from our website – simple, fast, secure.
Silent Network
We Designed It, We Custom-Built It & We Own The Network
Silent Circle Network provides encrypted communication tools that leverage cutting edge and simple to use apps and software. Here’s how we do it:
• Open Source Peer-Reviewed Encryption – Our founders are the inventors of the world’s most trusted encryption protocols: PGP, ZRTP, SCimp
• Multimillion dollar custom-built high definition network
• Geographic server redundancy – Servers located in Montreal and Toronto built with scalability for continued geographic expansion (Our Switzerland Network will come online Fall 2012)
• 100% dedicated network – No sharing
• Custom-built servers, PBXs and hardware – Ensuring security integrated through design
• E-Commerce, customer service, analytics and network monitoring software all custom built and designed to ensure security
• Device-to-Device Encryption – True peer-to-peer key negotiation with every communication session. Keys are destroyed at the end of every call eliminating the possibility of retroactive compromise
• Interactive Voice Authentication – Visual and vocal encryption verification eliminating the possibility of MiTM (man in the middle) attacks and a short authentication string (SAS)
• Peer Reviewed Encryption and Hashing Algorithms
– Elliptic Curve Cryptography (P-384)
– Advanced Encryption Standard (AES-256)
– Secure Hash Algorithm (SHA-256)Company website here.
—————————————————————-
Phil Zimmermann’s Silent Circle Builds A Secure, Seductive Fortress Around Your Smartphone
By Neal Ungereider
October 5, 2012
The cryptography legend is teaming up with two ex-Navy SEALs to offer encrypted phone calls, video conferencing, and text messages with no learning curve whatsoever. The target market? Businesspeople and government employees traveling abroad.
In the 1990s, cryptography pioneer and Pretty Good Privacy (PGP) creator Phil Zimmermann faced federal criminal investigation. His encryption software was so strong, it was charged, there was fear it violated arms trafficking export controls.